Key features
- User Management – Create, update, and delete user accounts.
- Role-Based Access Control (RBAC) – Assign predefined roles with granular permissions.
- Group Association – Manage user memberships across applications.
- OAuth2 Authentication – Secure authentication flows using JWT tokens.
- Performance Optimization – Uses in-memory caching for fast query handling.
- Observability – Integrated with OpenTelemetry for logging and tracing.
Role groups and permissions
User access in the Lerian ecosystem is controlled by role groups, defined per application (such as Midaz, Fee Engine, CRM, and others). Each role determines what users can see or do within a specific app. Roles are tied to permission sets, which are predefined combinations of actions and resources. These permission sets are managed centrally and can’t be customized.
Role levels
Each user is assigned one of the following roles:- Admin – Full access to all resources and system-level actions.
- Editor – Can create, update, and delete resources.
- Contributor – Can create and update resources, but can’t delete.
- Viewer – Read-only access; can view data but can’t make changes.
Roles are scoped per application. A user can have different roles across different apps. For example, Editor in Midaz, Viewer in CRM, and no role in Fee Engine.
| Role | Allowed Methods |
|---|---|
| Admin | Full control |
| Editor | GET, POST, PATCH, DELETE |
| Contributor | GET, POST, PATCH |
| Viewer | GET, HEAD |
Permission sets by application
Behind each role is a permission set that specifies which resources the user can access and what actions they’re allowed to perform. These sets are defined in theinit/casdoor/init_data.json file.
Expand the following section for the full list:
Permission table
| Name | Display Name | Resources | Actions |
|---|---|---|---|
| plugin-identity-editor-permission | Plugin Identity Editor Permission | applications, groups, users, update-password, reset-password | get, post, patch, delete |
| plugin-identity-default-permission | Plugin Identity Default Permission | update-password | patch |
| midaz-editor-permission | Midaz Editor Permission | accounts, organizations, ledgers, assets, asset-rates, portfolios, segments, balances, transactions, operations | get, post, patch, delete, head |
| midaz-contributor-permission | Midaz Contributor Permission | accounts, organizations, ledgers, assets, asset-rates, portfolios, segments, balances, transactions, operations | get, post, patch, head |
| midaz-viewer-permission | Midaz Viewer Permission | accounts, organizations, ledgers, assets, asset-rates, portfolios, segments, balances, transactions, operations | get, head |
| routing-editor-permission | Plugin Routing Editor Permission | account-types, transaction-routes, operation-routes | get, post, patch, delete |
| routing-contributor-permission | Plugin Routing Contributor Permission | account-types, transaction-routes, operation-routes | get, post, patch |
| routing-viewer-permission | Plugin Routing Viewer Permission | account-types, transaction-routes, operation-routes | get |
| plugin-fees-editor-permission | Plugin Fees Editor Permission | packages, fees, estimates | post, get, patch, delete |
| plugin-fees-contributor-permission | Plugin Fees Contributor Permission | packages, fees, estimates | post, get, patch |
| plugin-fees-viewer-permission | Plugin Fees Viewer Permission | packages, fees, estimates | get |
| plugin-crm-editor-permission | Plugin CRM Editor Permission | holders, aliases | post, get, patch, delete |
| plugin-crm-contributor-permission | Plugin CRM Contributor Permission | holders, aliases | post, get, patch |
| plugin-crm-viewer-permission | Plugin CRM Viewer Permission | holders, aliases | get |
| reporter-viewer-permission | Reporter Viewer Permission | templates, reports, data-source | get |
| reporter-contributor-permission | Reporter Contributor Permission | templates, reports, data-source | get, post, patch |
| reporter-editor-permission | Reporter Editor Permission | templates, reports, data-source | get, post, patch, delete |
How permissions are structured
All permission sets follow the same logic:| Role | Typical Methods |
|---|---|
| Viewer | GET, HEAD |
| Contributor | GET, POST, PATCH, HEAD |
| Editor | GET, POST, PATCH, DELETE, HEAD |
Plugin-level resources
Here’s a quick reference of the resources each plugin manages:| Plugin | Resource |
|---|---|
| Access Manager | applications, groups, users, update-password, reset-password |
| Midaz | accounts, organizations, ledgers, assets, asset-rates, portfolios, segments, balances, transactions, operations, account-types, transaction-routes, operation-routes |
| Fees | packages, fees, estimates |
| CRM | holders, aliases |
| Reporter | templates, reports, data-source |
Architecture and identity flow
Identity follows a clean architecture pattern with the following request flow: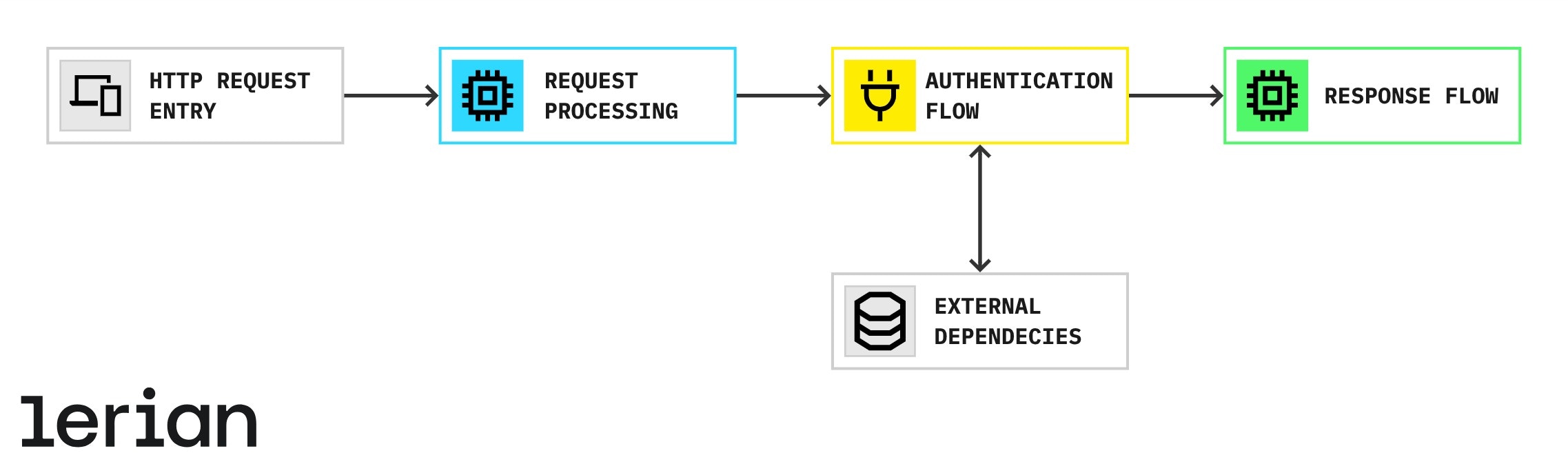
Figure 1. Identity Flow
Request flow
- HTTP request entry
- API endpoints process incoming requests.
- Middleware handles CORS, logging, and telemetry.
- Authorization middleware enforces access policies.
- Request processing
- Handlers validate input and extract parameters.
- The service layer executes business logic.
- The adapter layer translates service calls to the external IAM system.
- Authentication flow
- Client applications authenticate using OAuth2.
- JWT tokens are validated with embedded certificates.
- Permissions are enforced based on role definitions.
- Response flow
- Data is transformed into API response models.
- Standardized HTTP responses ensure consistency.
- Logging and telemetry track the request lifecycle.
External dependencies
- Primary storage – Centralized identity management system.
- Caching – Optimized with an in-memory data store.
- Tracing & monitoring – Integrated with OpenTelemetry.
- Deployment – Kubernetes for infrastructure management.
API overview
Identity provides centralized identity and access management for distributed applications. APIs support:- User account management and authentication.
- Role-based access control and permissions enforcement.
- Group and application identity operations.
Data storage and modeling
Identity doesn’t store data on its own—it connects with external systems to handle identity and caching.Primary storage
The service relies on an external identity management system as its main data store. It manages key entities like users, groups, and applications:- User entity
- Key properties: ID, first name, last name, username, email, hashed password, and group memberships.
- Mapping: Directly corresponds to user objects in the identity system.
- Operations: Supports create, read, update, and delete actions via API.
- Group entity
- Key properties: ID, name, display name, creation date, and associated users.
- Mapping: Directly corresponds to group objects in the identity system.
- Operations: Read operations available through API.
- Application entity
- Key properties: ID, name, description, client credentials, and creation date.
- Mapping: Directly corresponds to application objects in the identity system.
- Operations: Supports create, read, and delete actions via API.
Secondary storage
A document-based database is integrated to support additional data persistence needs.Caching
A caching layer is used to improve performance, managing temporary data efficiently. Connections and cache consumers are handled programmatically within Identity.Deployment & operations
- Scalability & reliability – Managed through Kubernetes.
- Observability – Integrated with OpenTelemetry.
- Security – Aligned with industry best practices for authentication and authorization.

