- OAuth2/OIDC-compliant authentication flows.
- Token issuance, validation, and refresh capabilities.
- User information retrieval according to OIDC standards.
- Permission enforcement for resources.
- Performance optimization through caching mechanisms.
Authentication and authorization flow
Auth implements several key authentication and authorization flows: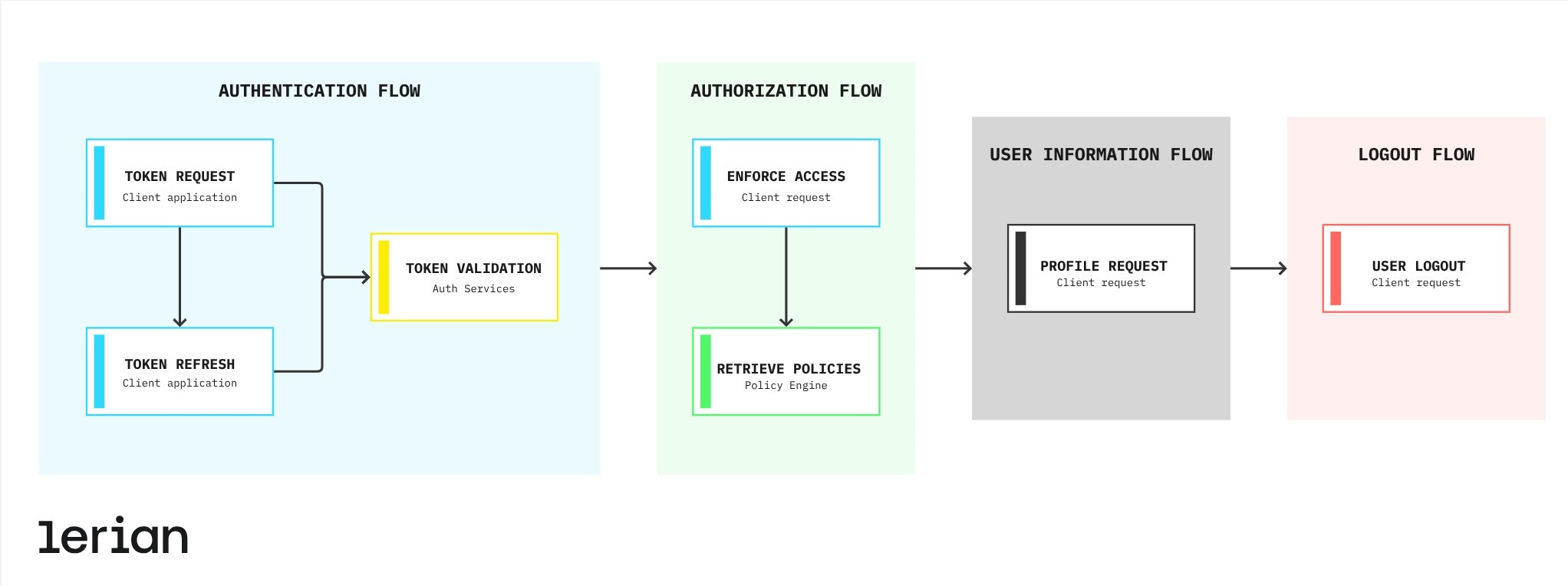
Authentication flow
Token request
-
Client applications request access tokens using either:
- Password grant (username/password for interactive users).
- Client credentials grant (for service-to-service authentication).
- The request is forwarded to the Identity Provider.
- Access token, refresh token, and optional ID token are returned.
Token refresh
- Client applications use refresh tokens to obtain new access tokens.
- The refresh token is validated via the Identity Provider.
- A new access token is issued.
Authorization flow
Enforce access
- Client requests access to a resource with an action.
- The subject ID is extracted from the token.
- The policy engine determines if the subject has permission.
- The result is cached for performance.
- The authorization decision is returned.
User information flow
Logout flow
API overview
Auth provides secure identity management and access control for Lerian applications. APIs support:- Authentication and token lifecycle management.
- Authorization and permission enforcement.
- User information retrieval.
Policy structure
The policy tables store permissions using the following pattern:Policy rule (ptype=‘p’):
identity-editor-role permission to perform the GET action on the users resource.
Group assignment (ptype=‘g’):
user123 to the identity-editor-role role.
Data storage and caching
Auth optimizes performance and security by leveraging a structured storage system and caching mechanisms:- Policy management: Stores access control policies for users and services.
- Token introspection cache: Caches token validation results to reduce redundant checks.
- Permission cache: Stores authorization decisions to improve response time.
- User policies cache: Maintains a map of resources and actions for efficient access control.
Testing & reliability
Auth undergoes continuous testing to maintain reliability and security. Tests cover:- Authentication and token validation flows.
- Access control enforcement.
- Performance and caching efficiency.

